質問 1:Service Consumer A sends a request message to Service A (1) after which Service A retrieves financial data from Database A (2). Service A then sends a request message with the retrieved data to Service B (3). Service B exchanges messages with Service C (4) and Service D (5), which perform a series of calculations on the data and return the results to Service A.
Service A uses these results to update Database A (7) and finally sends a response message to Service Consumer A (8). Component B has direct, independent access to Database A and is fully trusted by Database A.
Both Component B and Database A reside within Organization A.
Service Consumer A and Services A, B, C, and D are external to the organizational boundary of Organization A.
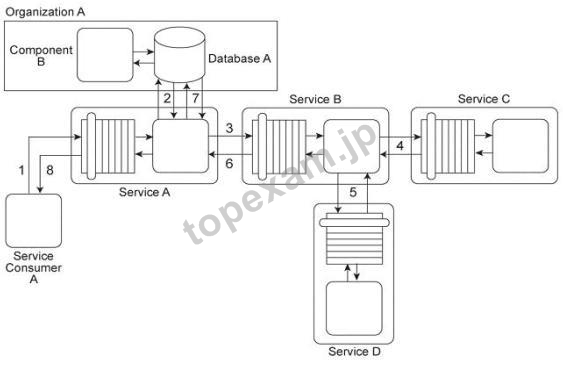
Service A has recently experienced an increase in the number of requests from Service Consumer A.
However, the owner of Service Consumer A has denied that Service Consumer A actually sent these requests. Upon further investigation it was determined that several of these disclaimed requests resulted in a strange behavior in Database A, including the retrieval of confidential data. The database product used for Database A has no feature that enables authentication of consumers. Furthermore, the external service composition (Services A, B, C, D) must continue to operate at a high level of runtime performance.
How can this architecture be improved to avoid unauthenticated access to Database A while minimizing the performance impact on the external service composition?
A. Service Consumer A generates a pair of private/public keys (Public Key E and Private Key D) and sends the public key to Service A.
Service A can use this key to send confidential messages to Service Consumer A because messages encrypted by the public key of Service Consumer A can only be decrypted by Service A The Data Origin Authentication pattern can be further applied so that Service A can authenticate Service Consumer A by verifying the digital signature on request messages. The Message Screening pattern is applied to a utility service that encapsulates Database A in order to prevent harmful input.
B. A utility service is established to encapsulate Database A and to carry out the authentication of all access to the database by Service A and any other service consumers.
To further support this functionality within the utility service, an identity store is introduced.
This identity store is also used by Service A which is upgraded with its own authentication logic to avoid access by malicious service consumers pretending to be legitimate service consumers. In order to avoid redundant authentication by services within the external service composition, Service A creates a signed SAML assertion that contains the service consumer's authentication and authorization information.
C. Implement a firewall between Service Consumer A and Service A.
All access to Service A is then controlled by the firewall rules. The firewall contains embedded logic that authenticates request messages and then forwards permitted messages to Service A.
Moreover, the firewall can implement the Message Screening pattern so that each incoming message is screened for malicious content. This solution minimizes the security processing performed by Service A in order to maintain the performance requirements of the external service composition.
D. The Brokered Authentication pattern is applied so that each service consumer generates a pair of private/public keys and sends the public key to Service A.
When any service in the external service composition (Services A, B, C, and D) sends a request message to another service, the request message is signed with the private key of the requesting service (the service acting as the service consumer). The service then authenticates the request using the already established public key of the service consumer. If authentication is successful, the service generates a symmetric session key and uses the public key of the service consumer to securely send the session key back to the service consumer. All further communication is protected by symmetric key encryption. Because all service consumers are authenticated, all external access to Database A is secured.
正解:B
質問 2:Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B.
Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and
C. Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E.
Service B uses the Service Inventory A identify store to validate the security credentials of Services A and C.
Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F.
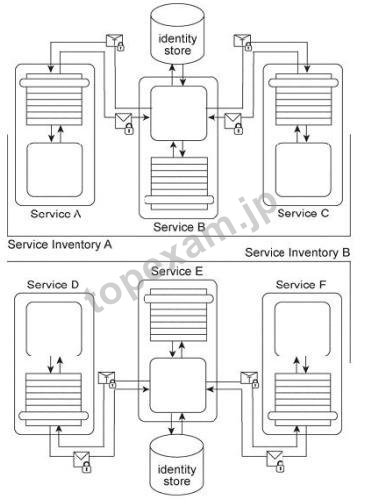
To date, the two service inventories have existed independently from each other. However, a requirement has emerged that the services in Service Inventory A need to be able to use the services in Service Inventory B, and vice versa.
How can cross-service inventory message exchanges be enabled with minimal changes to the existing service inventory architectures and without introducing new security mechanisms?
A. The Trusted Subsystem pattern is applied to encapsulate Services B and E using a central utility service that balances request and response messages exchanged between Services B and E, depending on which service inventory the messages originate from. The utility service also contains transformation logic to ensure that the SAML tokens issued by Services B and E are compatible. This guarantees that an issued SAML token can be used across Service Inventories A and B without further need for runtime conversion.
B. The individual domain service inventories need to be combined into one enterprise service inventory. The Service Perimeter Guard pattern can be applied to establish a contact point for request messages originating from outside the service inventory. Within the service inventory, services no longer need to be authenticated because they are all part of the same trust boundary.
C. Because SAML tokens cannot be used across multiple security domains, authentication brokers C and E need to be replaced with one single authentication broker so that one token issuer is used for all services across both of the service inventories.
D. The current security mechanism already fulfills the requirement because SAML tokens can be used across multiple security domains. The only change required is for each authentication broker to be configured so that it issues service inventory-specific assertions for SAML tokens originating from other service inventories.
正解:D
質問 3:Service A exchanges messages with Service B multiple times during the same runtime service activity. Communication between Services A and B has been secured using transport-layer security. With each service request message sent to Service B (1A. IB), Service A includes an X.509 certificate, signed by an external Certificate Authority (CA).
Service B validates the certificate by retrieving the public key of the CA (2A. 2B) and verifying the digital signature of the X.509 certificate. Service B then performs a certificate revocation check against a separate external CA repository (3A, 3B). No intermediary service agents reside between Service A and Service B.
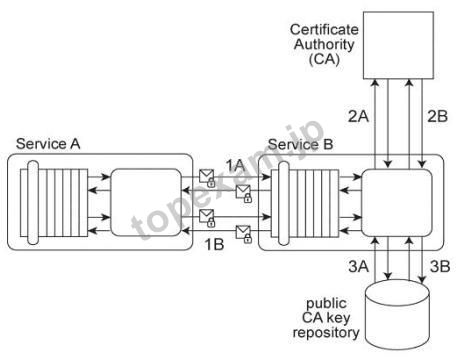
Service B has recently suffered from poor runtime performance plus it has been the victim of an access-oriented attack. As a result, its security architecture must be changed to fulfill the following new requirements: 1. The performance of security-related processing carried out by Service B when communicating with Service A must be improved. 2. All request messages sent from Service A to Service B must be screened to ensure that they do not contain malicious content.
Which of the following statements describes a solution that fulfills these requirements?
A. Eliminate the need to retrieve the public key from the Certificate Authority and to verify the certificate revocation information by extending the service contract of Service B to accept certificates only from pre-registered Certificate Authorities. This form of pre- registration ensures that Service B has the public key of the corresponding Certificate Authority.
B. Apply the Trusted Subsystem pattern to by introducing a new utility service. Because Service B is required to limit the use of external resources. Service A must ensure that no other services can request processing from Service B in order to prevent malicious content from infiltrating messages. This is achieved by creating a dedicated replica of Service B to be used by the utility service only. Upon receiving the request message and the accompanying security credentials from Service A.
the utility service verifies the authentication information and the validity of the X.509 signature. If the authentication information is correct, then the utility service replicates the code of Service B, performs the necessary processing, and returns the response to Service A.
C. Apply the Trusted Subsystem pattern by introducing a new utility service between Service A and Service B.
When Service A sends request messages, the utility service verifies the provided credentials and creates a customized security profile for Service A.
The security profile contains authentication and access control statements that are then inherited by all subsequent request messages issued by Service A.
As a result, performance is improved because Service A does not need to resubmit any additional credentials during subsequent message exchanged as part of the same runtime service activity. Furthermore, the utility service performs message screening logic to filter out malicious content.
D. Add a service agent to screen messages sent from Service A to Service B.
The service agent can reject any message containing malicious content so that only verified messages are passed through to Service B.
Instead of using X.509 certificates, use WS- SecureConversation sessions. Service A can request a Security Context Token (SCT) from a Security Token Service and use the derived keys from the session key to secure communication with Service B.
Service B retrieves the session key from the Security Token Service.
正解:D
一年間の無料更新サービスを提供します
君が弊社のSOA S90.20をご購入になってから、我々の承諾する一年間の更新サービスが無料で得られています。弊社の専門家たちは毎日更新状態を検査していますから、この一年間、更新されたら、弊社は更新されたSOA S90.20をお客様のメールアドレスにお送りいたします。だから、お客様はいつもタイムリーに更新の通知を受けることができます。我々は購入した一年間でお客様がずっと最新版のSOA S90.20を持っていることを保証します。
弊社は失敗したら全額で返金することを承諾します
我々は弊社のS90.20問題集に自信を持っていますから、試験に失敗したら返金する承諾をします。我々のSOA S90.20を利用して君は試験に合格できると信じています。もし試験に失敗したら、我々は君の支払ったお金を君に全額で返して、君の試験の失敗する経済損失を減少します。
安全的な支払方式を利用しています
Credit Cardは今まで全世界の一番安全の支払方式です。少数の手続きの費用かかる必要がありますとはいえ、保障があります。お客様の利益を保障するために、弊社のS90.20問題集は全部Credit Cardで支払われることができます。
領収書について:社名入りの領収書が必要な場合、メールで社名に記入していただき送信してください。弊社はPDF版の領収書を提供いたします。
弊社は無料SOA S90.20サンプルを提供します
お客様は問題集を購入する時、問題集の質量を心配するかもしれませんが、我々はこのことを解決するために、お客様に無料S90.20サンプルを提供いたします。そうすると、お客様は購入する前にサンプルをダウンロードしてやってみることができます。君はこのS90.20問題集は自分に適するかどうか判断して購入を決めることができます。
S90.20試験ツール:あなたの訓練に便利をもたらすために、あなたは自分のペースによって複数のパソコンで設置できます。
弊社のSOA S90.20を利用すれば試験に合格できます
弊社のSOA S90.20は専門家たちが長年の経験を通して最新のシラバスに従って研究し出した勉強資料です。弊社はS90.20問題集の質問と答えが間違いないのを保証いたします。

この問題集は過去のデータから分析して作成されて、カバー率が高くて、受験者としてのあなたを助けて時間とお金を節約して試験に合格する通過率を高めます。我々の問題集は的中率が高くて、100%の合格率を保証します。我々の高質量のSOA S90.20を利用すれば、君は一回で試験に合格できます。
TopExamは君にS90.20の問題集を提供して、あなたの試験への復習にヘルプを提供して、君に難しい専門知識を楽に勉強させます。TopExamは君の試験への合格を期待しています。
SOA Security Lab 認定 S90.20 試験問題:
1. Service A provides a data retrieval capability that can be used by a range of service consumers, including Service Consumer A, In order to retrieve the necessary data. Service Consumer A first sends a request message to Service A (1). Service A then exchanges request and response messages with Service B (2, 3). Service C (4, 5), and Service D (6.
7). After receiving all three response messages from Services B.
C. and D, Service A assembles the collected data into a response message that it returns to Service Consumer A (8).
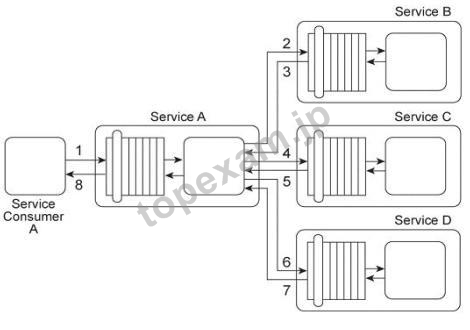
The Service A data retrieval capability has been suffering from poor performance, which has reduced its usefulness to Service Consumer A.
Upon studying the service composition architecture, it is determined that the performance problem can be partially attributed to redundant validation by service contracts for compliance to security policies. Services B and C have service contracts that contain the same two security policies. And, Service D has a service contract that contains a security policy that is also part of Service A's service contract.
What changes can be made to the service contracts in order to improve the performance of the service composition while preserving the security policy compliance requirements?
A) All policies are analyzed for similarities, which are then extracted and, by applying the Policy Centralization pattern, combined into a single policy definition. This "meta-policy" is then positioned to perform validation of the response message generated by Service A, prior to receipt by Service Consumer A.
If validation fails, an alternative error message is sent to Service Consumer A instead.
B) Apply the Policy Centralization pattern in order to establish a single security policy for the entire service composition. The redundant policies residing in the service contracts of Services A.
B, C and D need to be removed and grouped together into one master policy definition enforced by Service A.
This way, redundant policy validation is eliminated, thereby improving runtime performance.
C) Apply the Standardized Service Contract principle in order to remove redundancy within service contracts by ensuring that all four service contracts comply with the same policy standards. This further requires the application of the Service Abstraction principle to guarantee that policy definitions are sufficiently streamlined for performance reasons.
D) Apply the Policy Centralization pattern in order to establish two centralized policy definitions and ensure that policy enforcement logic is correspondingly centralized. The first policy definition includes the redundant security policies from Services A and D and the second policy definition contains the redundant security policies from Services B and C.
2. Services A, B, and C reside in Service Inventory A and Services D, E, and F reside in Service Inventory B.
Service B is an authentication broker that issues WS-Trust based SAML tokens to Services A and C upon receiving security credentials from Services A and
C. Service E is an authentication broker that issues WS-Trust based SAML tokens to Services D and F upon receiving security credentials from Services D and E.
Service B uses the Service Inventory A identify store to validate the security credentials of Services A and C.
Service E uses the Service Inventory B identity store to validate the security credentials of Services D and F.

To date, the two service inventories have existed independently from each other. However, a requirement has emerged that the services in Service Inventory A need to be able to use the services in Service Inventory B, and vice versa.
How can cross-service inventory message exchanges be enabled with minimal changes to the existing service inventory architectures and without introducing new security mechanisms?
A) The Trusted Subsystem pattern is applied to encapsulate Services B and E using a central utility service that balances request and response messages exchanged between Services B and E, depending on which service inventory the messages originate from. The utility service also contains transformation logic to ensure that the SAML tokens issued by Services B and E are compatible. This guarantees that an issued SAML token can be used across Service Inventories A and B without further need for runtime conversion.
B) The individual domain service inventories need to be combined into one enterprise service inventory. The Service Perimeter Guard pattern can be applied to establish a contact point for request messages originating from outside the service inventory. Within the service inventory, services no longer need to be authenticated because they are all part of the same trust boundary.
C) Because SAML tokens cannot be used across multiple security domains, authentication brokers C and E need to be replaced with one single authentication broker so that one token issuer is used for all services across both of the service inventories.
D) The current security mechanism already fulfills the requirement because SAML tokens can be used across multiple security domains. The only change required is for each authentication broker to be configured so that it issues service inventory-specific assertions for SAML tokens originating from other service inventories.
3.
A) A utility service needs to be created and positioned between Service A and the service consumer. The utility service can contain screening logic that can verify the service consumer's credentials and then forward the request message to the Private Database or to the Public Database, depending on the service consumer's access permissions.
Because each request message is evaluated by the database, no filtering of the returned data is necessary. The data is sent back to the consumer in a response message encrypted using symmetric key encryption.
B) The Service A logic needs to be modified to work with the two new databases. Service A needs to be able to access the Public Database and the Private Database when it receives a request message from a service consumer with private access permissions, and it must only access the Public Database when it receives a request message from a service consumer with public access permissions. Furthermore, any response messages issued by Service A containing private data need to be encrypted.
C) After the service consumer's request message is authenticated. Service A can generate a one-time symmetric encryption key that it sends to the service consumer. This key is encrypted by the public key of the service consumer. After the service consumer acknowledges the receipt of the one-time encryption key, Service A forwards the service consumer's data access request (and the corresponding credentials) to both databases.
After receiving the responses from the databases, Service A compiles the results into a single response message. This message is encrypted with the one-time key and sent by Service A to the service consumer.
D) The Service A architecture can be enhanced with certificate-based authentication of service consumers in order to avoid dependency on the identity store. By using digital certificates, Service A can authenticate a service consumer's request message and then forward the data access request to the appropriate database. After receiving the responses from the databases, Service A can use the service consumer's public key to encrypt the response message that is sent to the service consumer.
E) Each record in Database A is classified as either private or public. After Service A is invoked by a service consumer (1), it authenticates the request message using an identity store and retrieves the corresponding authorization (2, 3). Once authorized, the service consumer's request is submitted to Database A (4), which then returns the requested data (5) If the service consumer has private access permissions, all of the returned data is included in Service A's response message (6). If the service consumer has public access permissions, then Service A first filters the data in order to remove all unauthorized private data records, before sending to the response message to the service consumer (6).
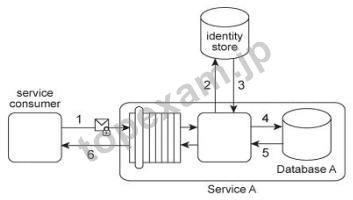
An investigation recently detected that private data has been leaked to unauthorized service consumers. An audit of the Service A architecture revealed that Service A's filtering logic is flawed, resulting in situations where private data was accidentally shared with service consumers that only have public access permissions. Further, it was discovered that attackers have been monitoring response messages sent by Service A in order to capture private data. It is subsequently decided to split Database A into two databases: one containing only private data (the Private Database) and the other containing only public data (the Public Database).
What additional changes are necessary to address these security problems?
質問と回答:
質問 # 1
正解: D | 質問 # 2
正解: D | 質問 # 3
正解: B、E |






 PDF版 Demo
PDF版 Demo







 品質保証TopExamは我々の専門家たちの努力によって、過去の試験のデータが分析されて、数年以来の研究を通して開発されて、多年の研究への整理で、的中率が高くて99%の通過率を保証することができます。
品質保証TopExamは我々の専門家たちの努力によって、過去の試験のデータが分析されて、数年以来の研究を通して開発されて、多年の研究への整理で、的中率が高くて99%の通過率を保証することができます。 一年間の無料アップデートTopExamは弊社の商品をご購入になったお客様に一年間の無料更新サービスを提供することができ、行き届いたアフターサービスを提供します。弊社は毎日更新の情況を検査していて、もし商品が更新されたら、お客様に最新版をお送りいたします。お客様はその一年でずっと最新版を持っているのを保証します。
一年間の無料アップデートTopExamは弊社の商品をご購入になったお客様に一年間の無料更新サービスを提供することができ、行き届いたアフターサービスを提供します。弊社は毎日更新の情況を検査していて、もし商品が更新されたら、お客様に最新版をお送りいたします。お客様はその一年でずっと最新版を持っているのを保証します。 全額返金弊社の商品に自信を持っているから、失敗したら全額で返金することを保証します。弊社の商品でお客様は試験に合格できると信じていますとはいえ、不幸で試験に失敗する場合には、弊社はお客様の支払ったお金を全額で返金するのを承諾します。(
全額返金弊社の商品に自信を持っているから、失敗したら全額で返金することを保証します。弊社の商品でお客様は試験に合格できると信じていますとはいえ、不幸で試験に失敗する場合には、弊社はお客様の支払ったお金を全額で返金するのを承諾します。( ご購入の前の試用TopExamは無料なサンプルを提供します。弊社の商品に疑問を持っているなら、無料サンプルを体験することができます。このサンプルの利用を通して、お客様は弊社の商品に自信を持って、安心で試験を準備することができます。
ご購入の前の試用TopExamは無料なサンプルを提供します。弊社の商品に疑問を持っているなら、無料サンプルを体験することができます。このサンプルの利用を通して、お客様は弊社の商品に自信を持って、安心で試験を準備することができます。
